Building Better PowerShell Dashboards
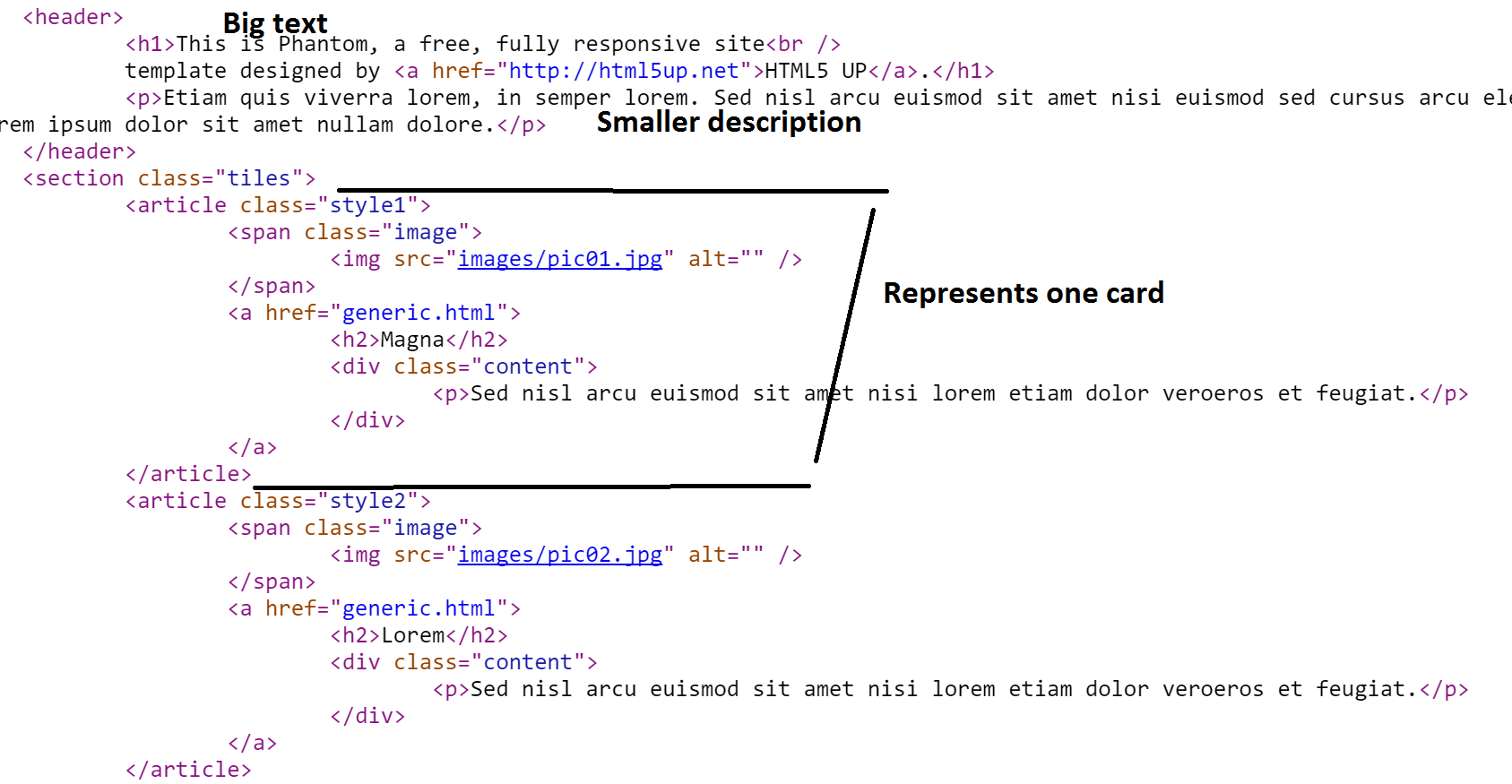
This post guides you through making cool HTML Dashboard directly with PowerShell Continue Reading...
SCOM: Quickly find Update Rollup Version
It’s SO tedious to track down the update rollup version of SCOM, as the SCOM console still doesn’t have this information available (only major releases!), so you end up looking through the registry or digging into files trying to look at the file version manually.
Continue Reading...Fix Hyper-V 'Account does not have permission' error
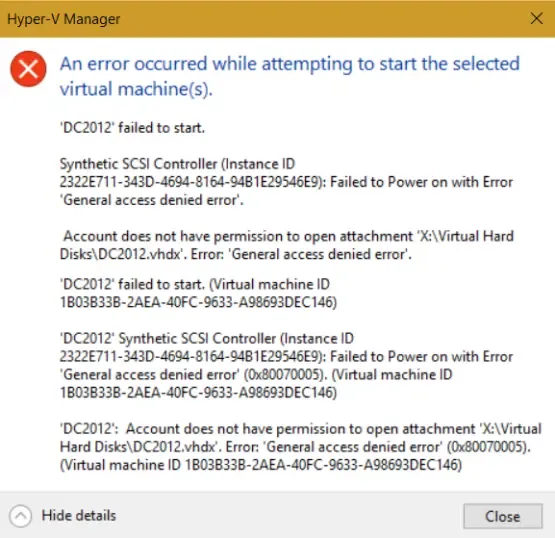
Today, I woke up to a nasty error in the FoxDeploy Hyper-V lab. All of my VMs were stopped, and wouldn't start! When I tried to start one, I'd see this error: > An error occurred while attempting to start the selected virtual machines: General Access Denied Error... > > VMName: Account does not have permission to open attachment
PowerClippy
Back with the release of Office ‘97 in November of 1996, Microsoft introduced a beloved new helper tool to assist users in navigating through the daunting changes in Microsoft Office,
Continue Reading...Coding for speed

In this post, we review some of the things we learned about coding for speed in the [Hadoop PowerShell challenge](http://foxdeploy.com/2016/03/01/powershell-challenge-beating-hadoop-with-posh/). The winners are at the end of this post, so zip down there to see if you won! We'll use the post to cover some of what we learned from the entries here. Here's our top three tips for making your PowerShell scripts run just that much faster! Continue Reading...
PowerShell Challenge - Beating Hadoop with Posh

This post sets the stage for the PowerShell Hadoop Challenge! Continue Reading...












